It’s just another Thursday morning. You wake up, brush your teeth, and start preparing your coffee. After some thirty minutes, you’re off to work.
The daily meeting went well, and everything seemed fine. But then, something strange starts happening.
Employees begin to notice some bizarre malfunctions in their computers and office equipment. Screens flicker with strange symbols, and cryptic messages appear on the internal communication platform. It’s written in a cryptic code that no one can decipher. Is it a warning, a threat, or something more sinister?
Everyone is trying to remain calm until more is known, but then the IT team stumbles upon files and data that have mysteriously disappeared. Critical documents, sensitive customer information, and confidential files have all vanished without a trace.
Uh-oh, this looks like a cyberattack.
A data breach is all but guaranteed now. And while the risks are assessed, you’re invited to participate in a meeting to try and identify the cause of the hacking.
You get to the whiteboard and start writing down and discussing the most common causes of cyberattacks that the criminals could have taken advantage of this time.
1. Passwords
Your company relies on passwords, so that could be one of the causes. After all, passwords turned 63 this year, having been introduced in 1960 at MIT.
Not only is it an outdated piece of technology, but it’s also fairly easy to hack. 80% of breaches involve brute force attacks or the use of lost or stolen credentials, both of which are targeted at passwords — you then remember reading at some point.
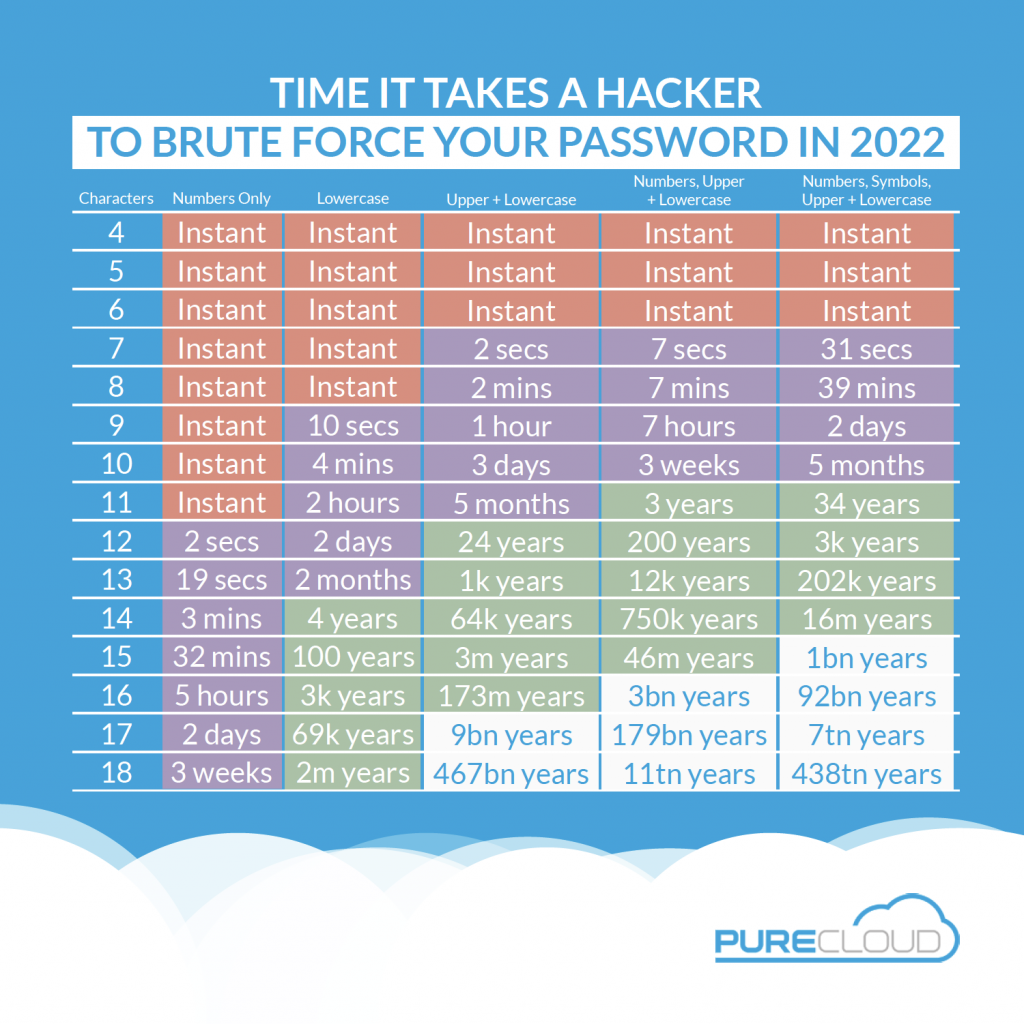
Similarly, passwords can get phished. As one of the most common fraud strategies, it could have happened to someone in the company.
Would events develop differently had you used passwordless authentication?
2. SIM Swapping
SIM swapping has often been in the media recently. Could someone have been SIM swapped?
SIM swapping is a fraudulent technique when a cybercriminal tricks your mobile network operators into issuing them a new SIM card with your phone number, thereby taking control of it.
The attacker could have used previously leaked data to trick a mobile network operator and take control of a phone number, and the damage has already been done before anyone noticed.
Recently, it was revealed that Vitalik Buterin, the co-founder of Ethereum, was a victim of SIM swapping. After cybercriminals gained control of his phone number through SIM swapping, they stole $691,000 from his Twitter followers.
But the scary part is that you don’t have to be “someone in high power” to become a target for SIM swappers. In fact, last year, the average amount of money stolen via SIM swapping in the UK was around only £2,500.
This has resulted in FBI issuing a warning about an increase in SIM swapping schemes that have caused $68 million in losses last year — a significant increase from $12 million in 2020.
To add to that, this incident could be one of the factors that render SMS OTP 2FA useless, although this type of two-factor authentication is vulnerable to other things too.
3. SMS OTP 2FA
In addition to being vulnerable to SIM swapping, SMS OTPs are susceptible to phishing and the tech comes with a flaw that criminals can take advantage of.
The codes can get phished through a fake web page, in the same way as passwords, while the SS7 technical flaw can be used to intercept or reroute an SMS message containing the one-time password.
You conclude that it was either one of those three or a combination of multiple factors. The team will have to investigate further, both the causes and the consequences.
After the meeting is over, you’re left wondering…
Huh… What are the chances?
After some googling, you find out higher than you would have guessed.
A 2022 case study that covered the US, Canada, UK, Australia, and New Zealand denotes that 76% of the respondents say their organization has suffered at least one cyberattack this year. To make matters worse, this constitutes an increase of 21% since 2020.
It makes you wonder what we can expect globally in the coming years if nothing changes when you glance over the data breach costs and the report sends your head spinning.
Globally, in 2023, the average cost of a data breach was $4.45 million, a 15% increase over three years.
Well, no way this keeps happening. You decide to research things that you could have done better, strategies that could have prevented this. And you come up with some great options that you decide to present to the team once the situation cools down.
Breaking the cybercrime spell: a happy ending
Having read about the things to look for in an authentication solution, you realize that you’d ideally need one that offers great security along with a frictionless user experience and maximum data privacy. That’s how you stumble upon IPification.
IPification is the leading global mobile IP address-based provider of authentication, user and transaction verification, and fraud prevention solutions, including SIM swap detection and eKYC. It’s passwordless and phishing-resistant!
IPification generates a unique Mobile ID key for each user, made of phone number, network, and device data. It relies on already existing mobile network operator tech infrastructure to authenticate users.
To authenticate, a user only needs to click once and the request is completed within milliseconds.
In cases where the user isn’t a subscriber of one of IPification’s many mobile network operator partners, there’s a backup solution: IPification IM Auth. It lets users verify their identities via WhatsApp, Viber, or Telegram, and it only takes another extra click to complete.
Most importantly, it can be integrated as part of a multi-factor authentication environment, something you’ll definitely be implementing after this incident.
You put together a presentation and look forward to presenting it to the team. It’s a great option for the future, ensuring something like this doesn’t happen again.
Good luck with the presentation! And if you need any additional information, be sure to contact us and schedule a free consultation.



