If you use the same password on multiple accounts, you share your email address like it’s nobody’s business, and you haven’t changed your phone number for ages — you are likely at risk.
What was the last time you checked how safe your accounts really are?
See for yourself: this useful website allows you to check whether your accounts have been compromised.
Feeling vulnerable? Now that we’ve got you listening, we’re here to give you some good news!
The most common types of frauds are quite simple to get around if you know what you’re dealing with. In this blog post, we’ll break down how these frauds take place and show you how to detect them quickly.
SIM swapping
Remember when those scandalous, offensive tweets started pouring from Jack Dorsey’s Twitter account, completely out of the blue?
Dorsey was a victim SIM swapping — also referred to as SIM-jacking, SIM hijacking, or SIM porting. Yeah, even tech moguls have to watch out for this sort of thing!
First, hackers migrate your phone number from your SIM card and phone to another card/phone. Social engineering your mobile phone provider into making this transfer isn’t that hard — a hacker can pretend to be you by telling a false story to get the support rep to transfer the number. If they arouse suspicion on the other end of the line, they can just hang up and try again with another support rep.
Once the number is successfully transferred, the attackers use it to gain access to all the internet accounts connected to that phone number. Usually, the first account targeted is Gmail, by “recovering” access to the account.
What and who is at risk?
This fairly simple technique can be used to target just about anyone. People often think that “nobody cares” about them enough to hack into their accounts — but piracy is very democratic and not being rich and famous doesn’t guarantee the hackers will leave you alone.
Extortion, theft, corporate espionage, or simply a malicious prank — anyone who hijacks your SIM card, for whatever reason, can access your:
- Cryptocurrency
- Social media accounts (especially of high-value: celebrities, influencers, accounts with a high number of organic followers, attractive @s)
- Sensitive data
- Personal information
- Mobile payment applications (or any other app connected to your phone number in some way)
- Online banking services
Mobile operators play a critical role in protecting their customers from SIM swapping. Check out our article about how to make this danger a thing of the past.
SIM swapping warning signs — how to know someone’s hijacking your number
In most cases, you will know right away if someone is trying to SIM-jack you.
If you’re lucky and your provider’s support rep managed to see through the attempt to migrate the phone number, you will receive a call from the rep, apologizing for the disconnection. You should state that you never spoke to them and ask them to pay special attention to your account — since someone is obviously trying to get unauthorized access to it!
Other SIM swapping signals include:
- Abrupt loss of cell reception — with no improvement even after you restart the phone or nudge your SIM card;
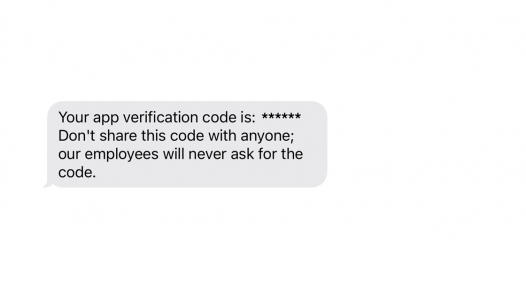
- Pop-ups and system notifications that the account was added to a new device, that you cannot access the phone-level account and need to re-enter your password or questions about logging in from another location or device;
- Emails stating that you have just signed in from another device or that you’ve made a transaction;
- SMS with a login code you’ve never requested.
Call from an unknown phone number
This is a well-known money-draining scam that’s been around for quite some time.
Many people tend to ignore the calls they receive from unknown phone numbers. You should avoid answering them too, if possible. The usual signs that the call from an unknown number is a scam are:
- Unexpected overseas and international calls, mostly from places where you have no connections
- Short-duration calls that try to get you to call them back to see what’s going on
- If you happen to return the call, the caller (or a taped message) will stall and try to keep you on the line as long as possible
Avoiding this scam is easy. Just don’t answer or return these calls, or check the area codes of unknown numbers before you consider answering.
“Unsubscribe” and other buttons in emails
A great part of the Internet users do not fall for the flashy, obtrusive CLICK HERE TO WIN IPHONE buttons anymore, but attackers use far sneakier methods in order to get you to click the CTA that downloads malware.
Assailants will spam you with emails, and mask them to look like the usual marketing emails you get from various companies that advertise their products this way. Every email should, by law, contain an option to unsubscribe and stop receiving such emails. Unfortunately, those very unsubscribe buttons are the real danger!
When you open the phishing email and try to unsubscribe, you will download the malware and have your data stolen.
Baiting is another way of using social engineering to trick specifically targeted people into clicking a button within an email. Baiting relies on curiosity and people’s cravings – and offering Trojan malware masked as a free gift.
Attackers will snoop around their victim’s social media profiles to learn about their interests and craft the email according to the info thus gathered. Let’s say the unsuspecting victim is an avid fan of a certain TV show. Including a link to watch a “leaked episode” as bait in the phishing trap would be very tempting. Sometimes, hackers using email don’t even have to investigate the individual profiles of their target victims. They often target a far bigger crowd by offering something that’s widely popular, expensive, and exclusive, such as Apple devices or the latest Game of Thrones episode.
How can you protect yourself from these emails?
Anti-spam filters usually stop phishing emails from even arriving in your inbox. Just in case, keep an eye on the emails you receive from the unknown companies and individuals. If an email seems at all suspicious, block the address in question and don’t look back.
Curbing fraud at its very roots
Asking the average user to constantly be on the lookout for possible security breaches, frauds and scams is too much, and its conflict with UX principles can have a negative effect on business.
Mobile phone numbers are currently one of the most personal pieces of data you could share online. Exposure can reveal a chilling amount of information about users with little effort. One of our recent blog posts goes into detail about the consequences of your personal mobile phone number becoming public.
Because the consequences are so serious, we firmly believe that the best idea is to leave security protocols and necessary mobile ID functionalities to the mobile network operators. By placing equal value on the UX, privacy, and security, IPification makes the dream of a digital world without password memorization come true!
By implementing our solution, mobile providers bring their customers a unique mobile ID system. It’s based on the phone number and device data, that detects any SIM or device change instantly. Our solution opens up new opportunities for revenue increase as well.
Read about our partnership with a member of Deutsche Telekom Group, and start visualizing the comfortable transition to a safer online presence for all the users.