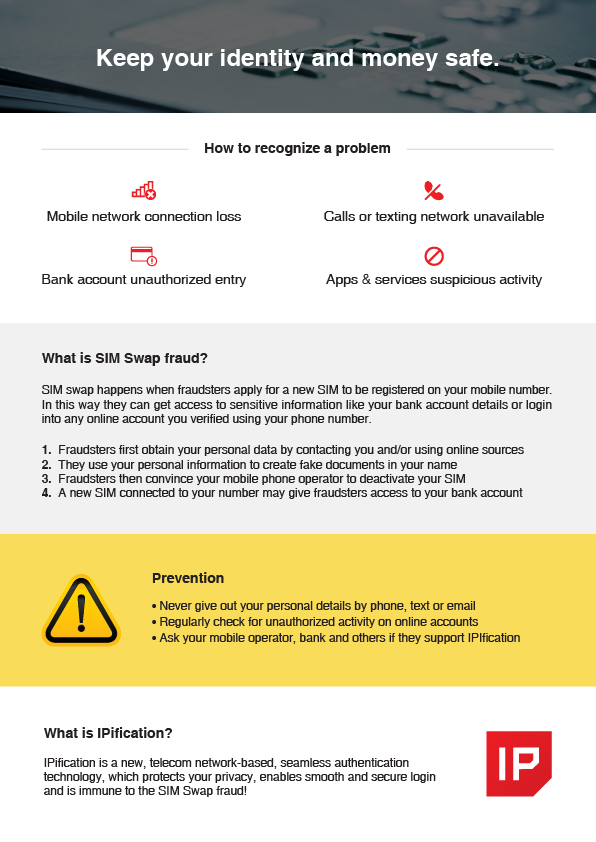
SIM Swapping is a worrisome scenario in which a fraudster uses your stolen identity to trick a mobile provider into issuing a new SIM card with your phone number.
The major problem with SIM-swapping isn’t that someone will just make you a huge phone bill, or buy a 1000-dollar new smartphone, no, that’s a 2007 scenario – it’s about severe bank and crypto account transfers once they obtain control of your apps.
SIM swapping has grown so fast in the last few years as the world is becoming mobile and as the value of overall mobile transactions and the value of individual mobile identity is soaring.
Fraudsters can see this potential and are looking for any security vulnerability to obtain personal gain. Right now, rising popularity of cryptocurrency is one of the premier drivers behind fast-spreading SIM-swapping events in the States and around the globe.
On 7th of November, KrebsOnSecurity published an interview with REACT Task Force, stating that SIM swappers are responsible for stealing hundreds of millions of dollars in cryptocurrency, making SIM swapping their number one priority at the moment.
SMS 2FA mobile authentication – an additional risk
SIM Swappers’ primary task is to obtain a user’s personal info like name, last name, social security number, and ID. Then they use that private information to trick the mobile network operator into reissuing the SIM card with the same phone number.
Once that SIM card is active, the original SIM card will be shut down, and the fraudster will try their best to login into the user’s banking or cryptocurrency app. They may have already obtained the user’s banking app password so the last line of defense may be 2FA mobile authentication.
If the mobile app is only using SMS based 2FA as the additional mobile authentication layer, the fraudsters already have all they need – the user’s mobile phone number. The presumption of the SMS-based 2FA is that a fraudster can only have one or two out of three elements – your personal ID, your password OR your mobile phone number. In SIM Swapping scenarios, the fraudsters can have all of the three elements, so once they prompt the SMS 2FA, the PIN code will arrive to the device they are controlling.
What can service providers do to detect and prevent SIM Swapping frauds
The same risks are related to all 2FA options relying on a user’s phone number, like VoIP or HTTP header enrichment.
What a service provider can do is include MFA (multi-factor authentication option) based on third-party apps like Google Authenticator, prompt the user to opt-in via physical authentication models or use an authentication model not dependent on any mobile phone number data to complete the authentication.
Third-party authentication apps are good when it comes to security but are a nightmare when it comes to user experience. Same goes with any physical authentication models – yes they are great in protecting your mobile ID but they do present one more thing you mustn’t lose track of.
The most convenient and most secure mobile authentication option that can protect users from SIM swapping related frauds is the mobile-network based authentication method not using any mobile number related info to complete the authentication. IPification is the authentication solution specifically designed for the mobile era. In that sense, IPification makes the authentication process seamless, without any user action and does not use any compromised and insecure communication channels.
What is far more important, the unique process of creating and authenticating the user mobile ID within IPification is designed so it can detect SIM swapping. This is impossible for almost any other 2FA or MFA solution. IPIfication technology uses a combination of different, encrypted data to create and assign a unique mobile ID to the specific user. Change in any element of a user’s mobile ID can indicate a security issue and therefore be used as an action trigger for the solution provider or the user.
Mobile Authentication Protecting Reputation of Mobile Network Operators
In any SIM Swapping scenario, mobile network operators are the most vulnerable link. Without them issuing the replacement SIM, SIM swapping would not be possible. The human factor is the one that is most unreliable in any fraud attempt. The employee of an operator can be blackmailed or they can be tricked into issuing SIM cards. Either way, operators are risking their reputation and major lawsuit losses.
The position of wireless providers in SIM swapping scenarios is dramatically impaired after the recent 220$ million lawsuit AT&T is facing over stolen cryptocurency. According to Turpin’s complaint document, his cell phone account was compromised due to “AT&T’s willing cooperation with the hacker, gross negligence, violation of its statutory duties, and failure to adhere to its commitments in its Privacy Policy.”
Aside from the multimillion figure in the lawsuit, this action underlines the importance and the responsibility of mobile network operators in today’s mobile world. Even if the human factor remains the only vulnerable point, SIM Swapping wouldn’t be possible if the users and the service providers implemented bulletproof, mobile 2-factor authentication.
This is one of the reasons why Mobile Connect and the Mobile Identity initiative were established within GSMA. The telecom world wants to protect its reputation by taking an active role in creating and promoting valuable authentication and mobile identity solutions. IPification has already been recognized as the game changer – positively affecting not just the telco and solution providers’ reputation but the revenue streams and user adoption.
In the mobile economy of today, mobile-based authentication solutions need to be the protectors and gatekeepers of the user’s identity. The best solutions are the ones not dependent on any user action nor the pieces of their physical identity. In other words, the perfect mobile authentication solution needs to exclude all human-related triggers and data in order to provide the most needed security. IPification is very much shaped by this notion.



