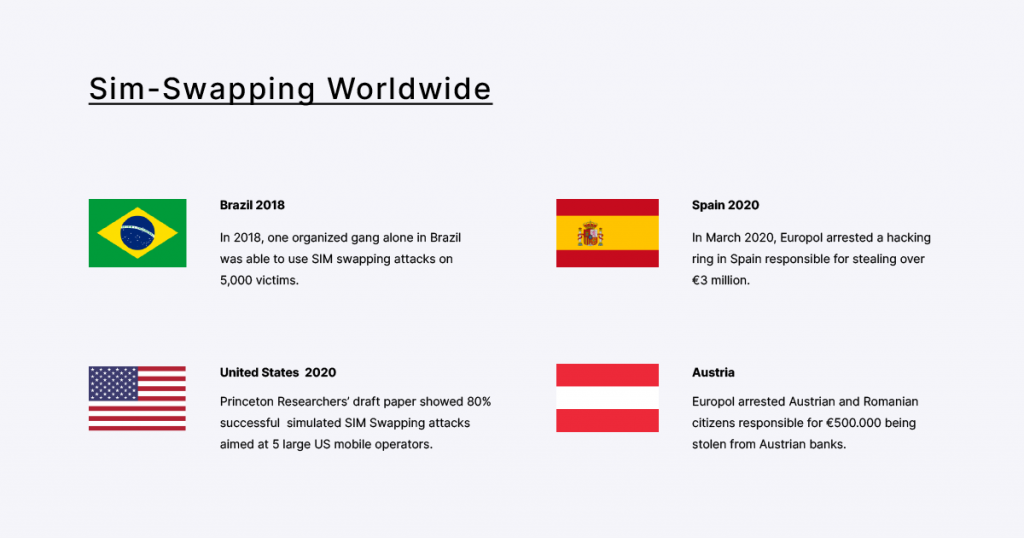
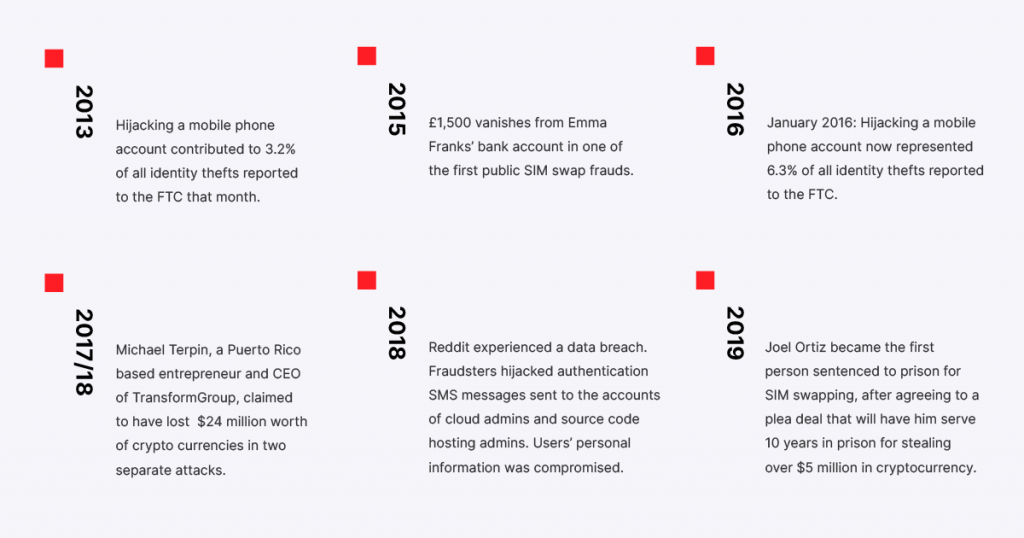
In 2015, £1,500 vanished from Emma Franks’ bank account in one of the first public SIM swap frauds. Since then, the scale of this fraud tactic has grown to incur millions of dollars of damage all around the world.
When fintech accounts will be but the only targets for SIM swappers, and when 80% of all SIM swap attacks are successful, it’s easy to see how preventing and detecting SIM swapping should be a priority for players in this industry.
Let me quickly bring you up to speed. What is SIM swapping?
SIM swapping is a hacking scenario where the fraudster gathers just enough of your personal data to trick your mobile network operator into issuing them a new SIM card with your phone number.
Once this new SIM card is active, the fraudster targets your two-factor authentication-protected accounts. Remember, they’ll be receiving all calls and SMS messages to your number, and most often, they’ll be long gone before you even notice that anything is wrong.
History Overview: SIM Swapping in FinTech
While we might associate hacking with technology by default, the majority of SIM swapping attacks succeed due to human error – and the worst part is that we’ll never be able to completely eliminate this.
The fraudster acquires your personal information such as your first and last name, social security number, date of birth, and ID. They then use this information to convince the MNO employees to issue them a new SIM card with your phone number. Alternatively, the employee could be blackmailed themself or even be in on the job.
And what happens next is not pretty.
In the victim’s case, they have lost their money, they have lost the trust they had in their mobile network operator, and the financial institution or fintech app at hand.
On the business side, these companies take huge blows to their reputation which could end up costing more than the direct damages they have to pay and those can be hefty, too.
The scope and scale of SIM swapping cases have been on steady growth in the last five years, culminating in the mainstream with the $220 million lawsuit AT&T faced over stolen cryptocurrency due to a successful SIM swap attack.
In fact, cryptocurrencies might be especially vulnerable to SIM swapping attacks.
Crypto Apps and mWallets Especially Vulnerable?
Cryptocurrencies and mWallets are usually the main targets for SIM swapping criminals. From what we know, cryptocurrency and mWallet theft via SIM swapping have been the largest cases.
In 2017/18, Michael Tepin, a Puerto Rico-based entrepreneur claimed to have lost $24 million worth of cryptocurrencies in two attacks which have resulted in the aforementioned AT&T lawsuit.
In 2019, a 20-year-old from Boston, Joel Ortiz became the first person sentenced to prison for SIM swapping after stealing more than $5 million in cryptocurrency from around 40 victims.
Just earlier this year, police arrested a European gang who used SIM swapping to steal more than $100 million in cryptocurrencies. And more of these cases pop up every day.
But, why are cryptocurrencies the main targets?
Because they are extremely hard to track. Once the fraudster transfers your funds, they become a part of the global accounts and there is little to no things you can do.
On top of that, the skyrocketing of Bitcoin in the last few months has made cryptocurrencies especially attractive today.
The final piece of the puzzle is that mWallets are usually protected with SMS OTP 2FA so when the fraudster overtakes your SIM, there isn’t much stopping them from stealing hard-to-track money.
With the pandemic speeding up the digital transformation and the increasing number of people onboarding these services, the risks tied to SIM swapping become overwhelming. And while Mobile Network operators keep improving their identity verification protocols, the human error factor will never be completely removed.
That’s precisely where technology should enter the picture, as the backup when a human error happens. Now, let me introduce you to IPification SIM Swap Detection.
How SIM Swap Detection Works
Because SIM Swap fraud is on the rise, we’ve decided to make the IPification SIM Swap Detection available as an individual, essential tool.
IPification assigns each user a unique mobile ID key based on their SIM card AND device data, and it verifies the user’s identity only against the complete mobile ID key.
When IPification SIM Swap detects a new SIM card, any authentication request is interrupted thus preventing any authentication-dependent transactions or action from being performed.
The service provider gets immediately notified that a new SIM card is detected so that they can take proactive action against potential fraud. Once the user confirms that they are indeed using a new SIM card, the authentication request continues.
IPification SIM Swap Detection is designed to prevent user account takeover and prevent crypto-theft, and I, for one, am very happy to see MNOs around the world integrating it on their networks to protect their users.
The process of integration IPification SIM Swap Detection is fairly simple –
1) Mobile operators can install our proprietary GMiD-Box on their networks to gain access to our SIM Swap Detection technology, along with the rest of our mobile authentication, one-click phone verification, and fraud prevention solutions, or;
2) Since we’ve made this tool available on its own, MNOs can implement it through their SIM swap API to prevent account takeover and any other theft.
As I already mentioned, the frequency and scale of SIM swapping fraud are on the rise. As such, it is crucial for companies to start implementing SIM swap prevention technologies – to protect their brand image, to protect the users’ trust, and to protect the users themselves.
If you’re looking for a partner that fully understands the scope of this issue and the impact it can have on all parties involved, look no further than IPification.
Let’s schedule a call.